Raspberry Pi Firewall: Open Ports List & Security Tips
Do you often wonder about the security of your Raspberry Pi and the potential vulnerabilities lurking within? Understanding and meticulously managing the open ports on your Raspberry Pi firewall is not merely advisable; it's an essential practice for anyone seeking to safeguard their network and the sensitive data it may harbor. The digital landscape is fraught with threats, and a misconfigured or poorly secured Raspberry Pi can quickly become a gateway for malicious actors.
The Raspberry Pi, a marvel of miniaturization and affordability, has rapidly become a favorite amongst hobbyists, students, and even professionals. Its versatility knows few bounds, finding application in everything from home automation and media servers to intricate industrial control systems. However, this very versatility introduces a critical need: secure communication channels. The default configuration of a Raspberry Pi, while functional, is not inherently secure. Numerous ports may be open by default, each representing a potential point of entry for unauthorized access. A firewall acts as the gatekeeper, meticulously controlling incoming and outgoing network traffic, and understanding its configuration is paramount.
Before diving into the specifics of port management, it's crucial to grasp the fundamental concepts. A port is a virtual endpoint on a network device, acting as a specific channel for communication. Each port is identified by a number, ranging from 0 to 65535. Certain port numbers are reserved for specific services; for example, port 80 is the standard for HTTP (web traffic), and port 22 is commonly used for SSH (secure shell) access. A firewall operates by examining network traffic and determining whether to allow or deny it based on predefined rules. These rules specify which ports are open (allowing traffic) and which are closed (blocking traffic).
Understanding which ports are open on your Raspberry Pi firewall is the first step in hardening its security. You can use several tools to accomplish this. One of the most common is `nmap` (Network Mapper), a powerful and versatile port scanner. `nmap` can identify open ports, determine the services running on those ports, and even attempt to detect the operating system. To use `nmap`, you'll first need to install it if it's not already present. On Debian-based systems like Raspberry Pi OS, you can install it using the command: `sudo apt update && sudo apt install nmap`.
Once `nmap` is installed, you can use it to scan your Raspberry Pi. For a basic scan of all TCP ports, you can use the command: `nmap -p 1-65535 `. Replace `` with the actual IP address of your Raspberry Pi. This will scan all 65,535 TCP ports and report which ones are open. Be aware that this can take a considerable amount of time.
A more targeted approach is often more efficient. For example, if you suspect that SSH is running, you can scan port 22 specifically: `nmap -p 22 `. Similarly, you can scan specific ranges of ports or scan for specific services. `nmap` offers a plethora of options; consult its manual (`man nmap`) for more details.
Another useful tool for checking open ports is `netstat` (Network Statistics). Although `netstat` is considered a legacy tool and is often replaced by `ss` (Socket Statistics), it is still frequently used and readily available on most systems. To see a list of listening ports, you can use the command: `sudo netstat -tulnp`. The `-t` flag specifies TCP ports, `-u` specifies UDP ports, `-l` shows listening ports, `-n` displays numerical addresses and ports (avoiding DNS resolution), and `-p` shows the process ID and name of the program using the port.
The output of `netstat` will display a list of listening ports, along with the associated programs. This is useful for quickly identifying which services are active on your Raspberry Pi. Remember to interpret the output carefully; some ports may be open for legitimate reasons, while others may indicate a vulnerability.
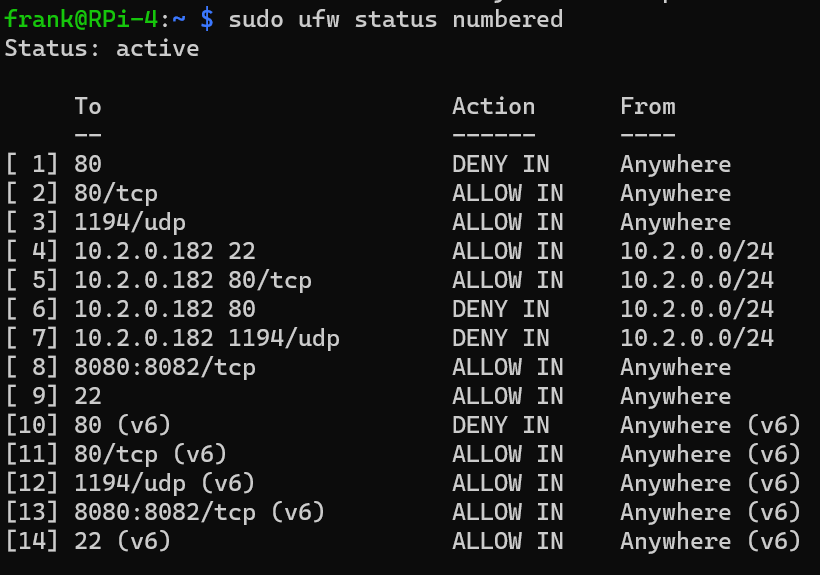
The primary tool for managing your Raspberry Pi's firewall is `iptables`. `iptables` is a powerful, command-line-based firewall that allows you to define complex rules for controlling network traffic. However, `iptables` can be complex to configure, and a misconfiguration can inadvertently block legitimate traffic or leave your system vulnerable. Therefore, its essential to proceed with caution and understand the implications of each rule you create.
To view the current `iptables` rules, you can use the command: `sudo iptables -L`. This will display the rules in the default "filter" table. You can also view the rules in the "nat" (Network Address Translation) and "mangle" tables using the `-t` option (e.g., `sudo iptables -t nat -L`). The default rules typically allow all outgoing traffic and block all incoming traffic by default, except for established and related connections (connections that are already established or are related to an established connection). This provides a basic level of security.
To add a rule to `iptables`, you use the `iptables -A` command, where `-A` appends the rule to the chain. For example, to allow incoming SSH traffic on port 22, you would use the command: `sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT`. Lets break down this command: `-A INPUT`: Appends the rule to the INPUT chain (for incoming traffic). `-p tcp`: Specifies the protocol as TCP. `--dport 22`: Specifies the destination port as 22. `-j ACCEPT`: Specifies the action to take: accept the traffic.
For UDP, you would use -p udp. To block traffic, you would use `-j DROP` or `-j REJECT` (reject sends an ICMP message back to the sender, while drop silently discards the packet).
Once youve configured your `iptables` rules, its crucial to save them so they persist across reboots. The method for saving `iptables` rules varies depending on your operating system and how youve installed `iptables`. On Raspberry Pi OS, you can typically use the `iptables-persistent` package, which allows you to save your rules automatically. To install it, run: `sudo apt install iptables-persistent`. During the installation, you will be asked if you want to save the current IPv4 and IPv6 rules; answer 'yes' to both. Afterwards, your `iptables` rules will be automatically loaded each time the system boots. Other methods involve saving the rules to a file and restoring them at boot using a startup script.
Firewalld is another firewall management tool available on some Linux distributions, including Fedora and CentOS. It is often considered more user-friendly than `iptables` because it provides a simpler interface and uses zones to manage network configurations. However, it is not commonly used on Raspberry Pi OS, which primarily uses `iptables`. If you are using a different distribution or are considering using Firewalld, research how to install and configure it appropriately for your system.
Managing open ports isn't just about blocking unwanted traffic; it's also about ensuring that necessary services function correctly. For example, if you're running a web server (like Apache or Nginx) on your Raspberry Pi, youll need to have port 80 (HTTP) or 443 (HTTPS) open to allow external access to your website. Similarly, if you're using SSH to remotely access your Raspberry Pi, youll need port 22 open. Opening these ports should be done with careful consideration, and only if absolutely necessary.
Regularly reviewing and auditing your open ports is crucial for maintaining the security of your Raspberry Pi. This involves periodically running port scans to identify any unexpected open ports or services that you might not be aware of. It's also important to keep your system updated with the latest security patches to mitigate potential vulnerabilities. Security updates frequently address vulnerabilities that could be exploited through open ports.
Beyond simply managing the ports themselves, it's essential to harden the services running on those ports. For example, if you have SSH enabled, consider changing the default SSH port (port 22) to a non-standard port. This can help to reduce the likelihood of automated attacks. Also, use strong passwords and enable two-factor authentication (2FA) for SSH and other services to protect against unauthorized access. Furthermore, configure services to use encryption where possible (e.g., HTTPS for web traffic) to protect the confidentiality of transmitted data.
Another critical aspect of securing your Raspberry Pi is understanding the services that are running on it. Each service represents a potential attack vector, and it is essential to know what services are running, why they are running, and whether they are necessary. Use the `ps` command (process status) to view running processes and identify any unfamiliar or suspicious services. Investigate any unknown processes and determine if they are legitimate or potentially malicious.
Consider using a host-based intrusion detection system (HIDS) on your Raspberry Pi. A HIDS monitors system activity and alerts you to suspicious behavior, such as unauthorized access attempts, suspicious file modifications, or unusual network activity. There are several HIDS options available, including Snort and Suricata, which can be configured to monitor your Raspberry Pi's activity and alert you to potential security breaches.
Moreover, consider using a network intrusion detection system (NIDS) on your network. A NIDS monitors network traffic for suspicious activity and can alert you to potential attacks targeting your Raspberry Pi or other devices on your network. Common NIDS solutions include Snort and Suricata, which can be deployed on a separate device (e.g., a dedicated Raspberry Pi) or virtual machine.
Regularly back up your Raspberry Pi's configuration and data. This is crucial in case of a security breach or system failure. Store your backups in a secure location, preferably off-site. Backups allow you to quickly restore your system to a known good state and minimize the impact of a security incident.
The concept of "least privilege" is a fundamental principle of security. Apply this principle to your Raspberry Pi by limiting the privileges of user accounts and services. For example, do not run services as the root user unless absolutely necessary. Create separate user accounts with the minimum required privileges for each service.
Staying informed about the latest security threats and best practices is essential. Subscribe to security newsletters, read security blogs, and participate in online forums to stay up-to-date on the latest vulnerabilities and attack techniques. The security landscape is constantly evolving, so continuous learning is crucial. Consider also reading the official documentation for your Raspberry Pi OS and the software you are using, as it often contains important security recommendations.
In the event of a security incident, it is vital to have an incident response plan in place. This plan should outline the steps you will take to contain the incident, investigate its root cause, and recover from it. Having a well-defined plan can help you to minimize the damage and restore your system to a secure state as quickly as possible. Its worth spending time to prepare a plan even before you need it.
Here's a table to summarize the key commands and tools:
| Tool/Command | Description | Purpose |
|---|---|---|
nmap | Network Mapper - a port scanner | Identify open ports and services running on those ports |
netstat | Network Statistics | List listening ports and the associated processes |
iptables | Command-line firewall utility | Configure and manage firewall rules |
sudo apt update && sudo apt install nmap | Command to install nmap on debian based systems | Installs the Nmap package on the system, enabling the user to use it |
iptables -L | View current iptables rules | Displays the active firewall rules configured for the system, providing a snapshot of how network traffic is currently being managed. |
iptables -A INPUT -p tcp --dport 22 -j ACCEPT | Example iptables rule: allow SSH traffic | Adds a rule to the INPUT chain to accept TCP traffic on port 22 (SSH) |
The effective management of open ports on your Raspberry Pi is not merely a technical task; it's an ongoing commitment to safeguarding your data, protecting your network, and maintaining the integrity of your system. It involves a continuous process of monitoring, auditing, and adapting your security measures to the ever-changing threat landscape. By implementing the strategies outlined in this article, from utilizing tools like `nmap` and `iptables` to practicing secure configurations, regular audits, and incident response planning, you can dramatically reduce your risk profile and ensure that your Raspberry Pi remains a secure and reliable platform for all your digital endeavors. The vigilance required to protect your system is always worth the effort.